TLS/SSL Encryption Explained
Using symmetric & asymmetric encryption at the same time
In the article on encryption, symmetric & asymmetric key encryption was explained, as well as the use cases for both types of encryption.
The main strength of symmetric key encryption is that it is computationally easier and faster to encrypt and decrypt data using a single key. The weakness of symmetric key encryption is that if the key is exposed, your data is no longer securely encrypted. So, if you needed to share the key with an external party, there is a risk that the key could be exposed, leaving your data at risk of being decrypted.
With asymmetric key encryption, this is not a problem since two separate keys are used - the public key to encrypt data and the private key to decrypt data. The public key can be easily shared with anyone and poses no risk to your data being decrypted, since the private key is needed for decryption. The drawback of asymmetric key encryption is that the encryption and decryption process is slower and more complicated.
TLS/SSL encryption uses both symmetric & asymmetric keys for encrypting data in transit. It first uses asymmetric key encryption to establish a secure channel for exchanging the symmetric key, and then switches to symmetric key encryption for the rest of the session. This process will be explained in greater detail in this article. By combining both symmetric & asymmetric key encryption, TLS/SSL ensures secure encryption of data without the computational complexity and increased time needed for asymmetric encryption.
What is TLS/SSL?
TSL (Transport Layer Security) and SSL (Secure Sockets Layer) are often used interchangeably to mean the same thing. But when people say SSL, they often mean TLS.
TLS is generally considered more secure than SSL due to several improvements made to the protocol, such as stronger cryptographic algorithms. Due to security concerns with SSL, most modern web browsers and applications have dropped support for SSL and only support TLS. As a result, TLS has become the standard for secure communication over the internet.
Using Symmetric & Asymmetric Encryption at the Same Time
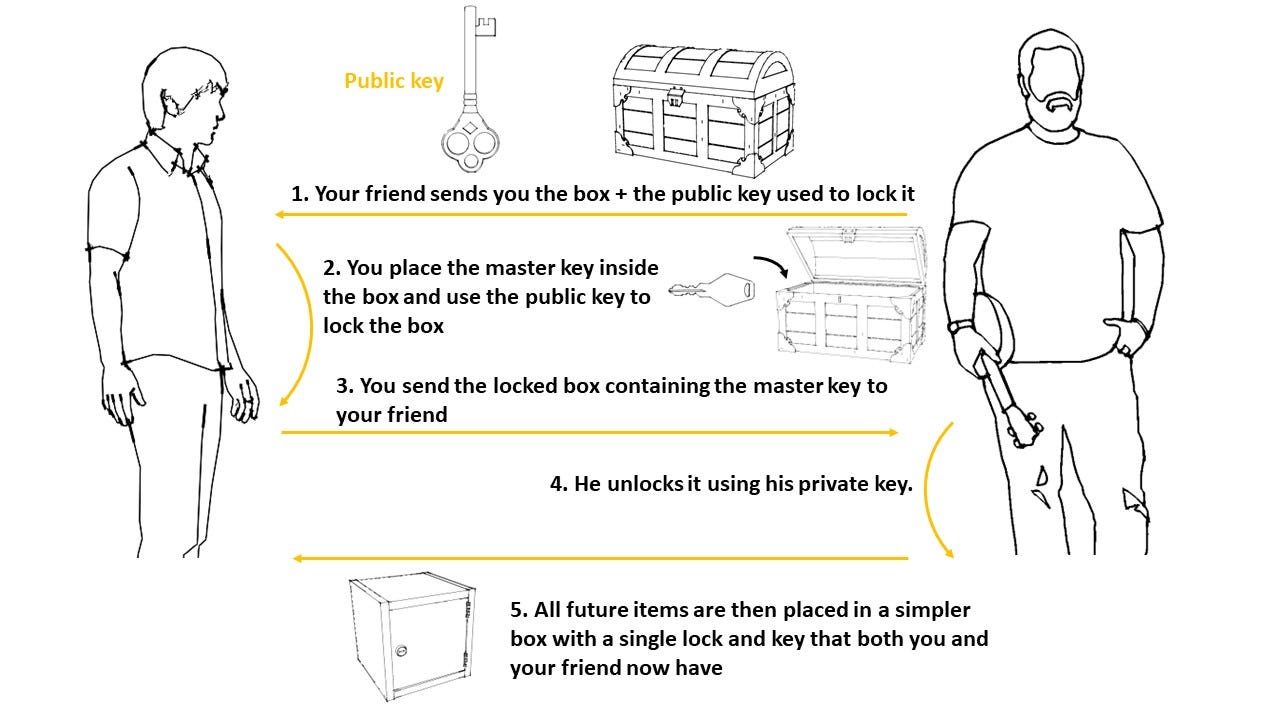
Lets say you want to securely send a parcel to your friend. However, you don’t want to keep using the special indestructible box that has two keyholes and two locks. It is expensive, heavy and impractical to use for frequent communications. You still want to use an indestructible box, but one that is simpler, with a single lock and key.
However, if you are using a box with only a single lock and key, you now need to figure out how to securely share the key for that simpler box with your friend. Since the same key is used to both open and lock it, you cant just send the key to your friend without somehow protecting it first. If the key is intercepted and a copy is taken by someone, they can now open your box and take what is inside.
How can you securely share this key with your friend so that you can use this simpler box for future communication?
First, your friend sends the box with the two locks plus the public key used to lock it. You don’t however want to keep using this box. You will only use this box once - to transfer the key for another simpler box that you will use for future exchanges
You place the master key that will be used in future exchanges inside this box and lock it with the public key sent by your friend
You send the locked box which contains a copy of the master key inside back to your friend
Your friend uses his private key to open the box. Now you both have the master key and can be sure no one else has it since it was sent in a secure box
All future items are then placed in this simpler box with a single lock and key which can be opened and locked using the master key you just sent to your friend.
TLS/SSL Encryption Sequence
The analogy in the previous section neatly maps to how TLS/SSL encryption actually works. There are some prerequisite steps which are ignored in this analogy, like creating a TCP connection and the server sending its certificate (Steps 1 and 2 below). Also, Step 6 is a simplification of the process. In reality, the master key is used to generate a further set of keys that the client and server will use to encrypt and decrypt messages and also to authenticate that the messages were indeed sent by the client and server. To read more of the low level detail, I’d recommend Chapter 8 of “Computer Networking” by Kurose & Ross.
But, at a high level, the sequence is as follows:
Client establishes TCP connection with the server
Client verifies that the server is who it says it is - server sends certificate which has the public key. The accompanying private key remains with the server
Client creates a master secret key and uses the servers public key to encrypt it. This master secret key is a symmetric key so the same key is used for encryption and decryption
Client sends the encrypted master secret key to the server
Server decrypts the encrypted master key using its private key
All future messages between client and server now use the symmetric master key to encrypt and decrypt messages
Best of Both Worlds
Using both symmetric and asymmetric key encryption gives you the speed of symmetric key encryption without compromising on the extra security provided by asymmetric key encryption. Nothing comes for free of course. With TLS, there is an added layer of complexity since you need to first use asymmetric keys to establish a secure connection before exchanging the symmetric key for future communication. By using both symmetric & asymmetric encryption, TLS/SSL gets the best of both worlds with limited downside.